Posts
Showing posts with the label Confronting Cyber Stalking
FEATURED POST
What should I do if I accidentally clicked on a suspicious link?
- Get link
- X
- Other Apps
By
Sagar Rajbanshi
On

If you've accidentally clicked on a suspicious link, it's important to act quickly to protect your information and your device from potential threats. Image for illustration purposes | Accidentally clicked on a suspicious link PLAY TO LISTEN Also read | Identifying Phishing Scams: A Guide to Staying Secure Online Here's a step-by-step guide on what to do: 1. Disconnect from the Internet: To prevent any potential malware from communicating with its server, disconnect your device from the internet. If you're on a desktop with a wired connection, unplug the ethernet cable. For Wi-Fi connections, turn off the Wi-Fi on your device. 2. Close the Suspicious Page: Immediately close the tab or window where the suspicious link took you. If possible, close your browser entirely. 3. Run a Sec...
Protecting Yourself During a Service Outage: Proactive Measures and Best Practices
- Get link
- X
- Other Apps
By
Sagar Rajbanshi
On

Service outages, like the one experienced by Microsoft, can occur unexpectedly and have significant consequences for users. While it's impossible to prevent all potential disruptions, there are several steps users can take to protect themselves and minimize the impact of such events. Here are some proactive measures and best practices to consider: Image for illustration purposes | Proactive Measures and Best Practices during a Service Outage PLAY TO LISTEN Stay Informed: Follow the service provider's official communication channels, such as their website, social media, or dedicated status pages, to get real-time updates about the outage and recovery efforts. Also read | Identifying Phishing Scams: A Guide to Staying Secure Online Backup Your Data: Regularly back up important data to multiple locations, such as an external hard drive and a cloud storage service. This ensures that you can acc...
What is CrowdStrike and How it works?
- Get link
- X
- Other Apps
By
Sagar Rajbanshi
On

In the rapidly evolving world of cybersecurity, companies like CrowdStrike have become synonymous with cutting-edge protection and incident response. Founded in 2011, CrowdStrike has been at the forefront of cybersecurity, offering cloud workload protection, endpoint security, threat intelligence, and cyberattack response services. Their innovative approach has earned them recognition as a leader in the industry, with a significant customer base that trusts their solutions for safeguarding critical data and infrastructure. Image for illustration purposes | CrowdStrike PLAY TO LISTEN However, the cybersecurity landscape is fraught with challenges. Recently, CrowdStrike made headlines when a serious IT outage, reportedly sparked by an issue at the company, caused widespread disruptions across various sectors, including airlines, banking, and media companies. This incident underscores the complex and interconnected n...
Understanding the Microsoft Outage: A Comprehensive Overview
- Get link
- X
- Other Apps
By
Sagar Rajbanshi
On
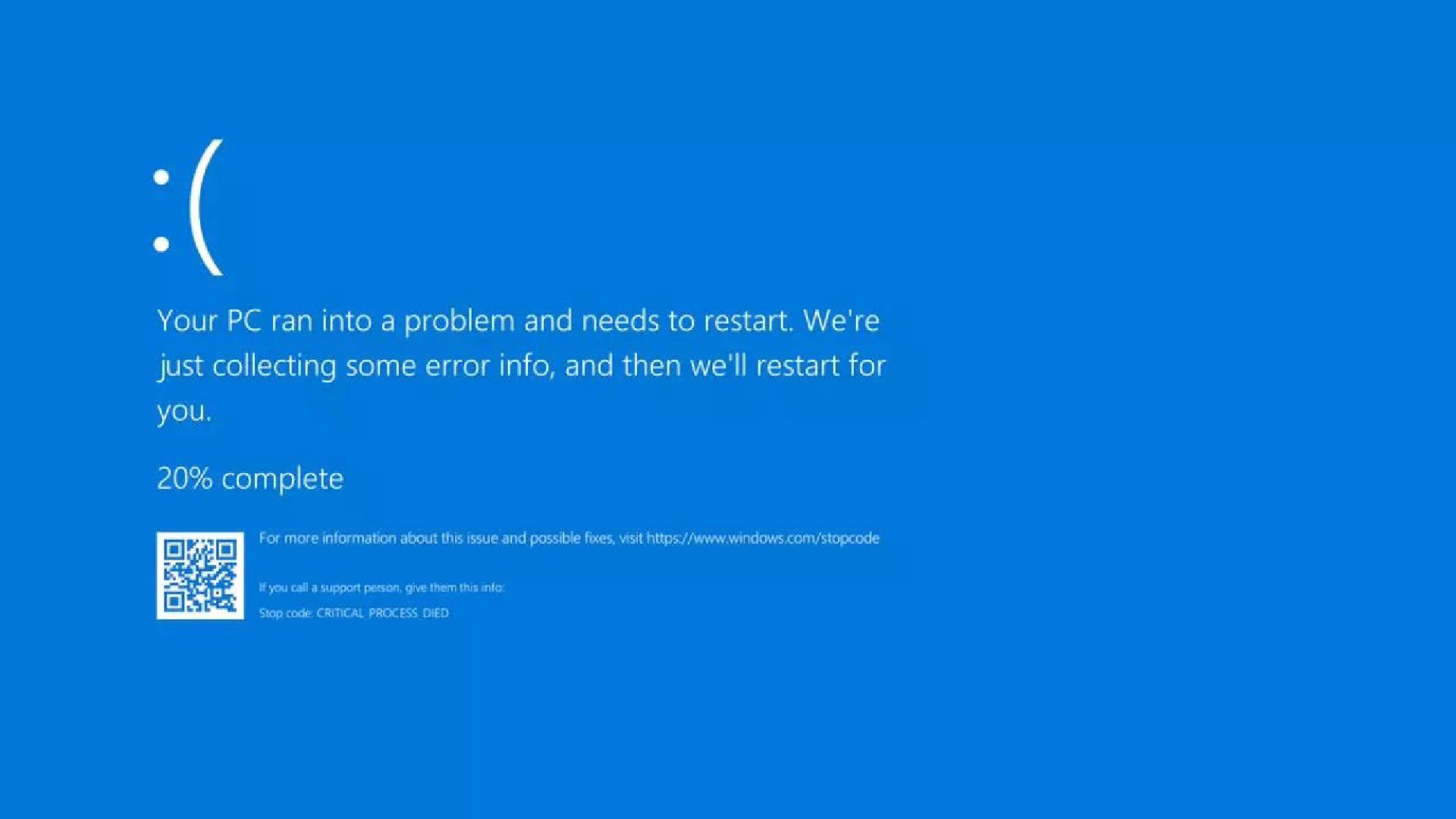
On July 19, 2024, the world experienced a significant disruption when Microsoft services encountered a massive global outage. This event caused widespread chaos, affecting various sectors from emergency services to financial institutions. The root cause of this outage was traced back to a faulty cybersecurity update from CrowdStrike, a company that provides security for many Windows PCs and services globally. Image for illustration purposes | Microsoft's massive outage PLAY TO LISTEN The impact was immediate and far-reaching. Emergency 911 lines were reported down across multiple states in the US, starting with Alaska. This situation prompted authorities to provide alternative emergency contact numbers to ensure public safety. The outage also grounded flights, with airports from New Zealand to the UK reporting issues, especially with scanning technology failing to register passengers' boarding passes. The Lo...
Identifying Phishing Scams: A Guide to Staying Secure Online
- Get link
- X
- Other Apps
By
Sagar Rajbanshi
On

In the digital age, phishing scams have become a prevalent threat to online security, attempting to trick individuals into divulging sensitive information. Image for illustration purposes | Identifying Phishing Scams PLAY TO LISTEN Also read | Microsoft's massive outage explained in 10 points. Recognizing the signs of a phishing scam is crucial for protecting personal data and maintaining privacy. Here are some common indicators that an email or message might be part of a phishing attempt: 1. Unfamiliar Tone or Greeting: Phishing emails often start with a generic greeting or may use a tone that doesn't match previous communications from the same sender. 2. Grammar and Spelling Errors: Professional organizations typically ensure their communications are free of errors. Frequent grammar or spelling...
Microsoft's massive outage explained in 10 points
- Get link
- X
- Other Apps
By
Sagar Rajbanshi
On

The recent global outage that affected Microsoft services has been a significant event, causing widespread disruption. Image for illustration purposes | Microsoft's massive outage PLAY TO LISTEN Also read | Identifying Phishing Scams: A Guide to Staying Secure Online Here's a detailed breakdown of what happened, why it happened, and the current status of recovery efforts: The Trigger: A cybersecurity update from CrowdStrike, intended to protect systems, unfortunately contained a flaw. This update inadvertently caused a series of events leading to the outage. Affected Services: The outage impacted a variety of Microsoft services, including Azure and 365 platforms. Essential applications like Outlook, Teams, SharePoint, and OneDrive experienced disruptions. Th...
CONFRONTING CYBER STALKING
- Get link
- X
- Other Apps
By
Sagar Rajbanshi
On

The cyber Helpline and advice on UNDERSTANDING and PROTECTING YOUR CYBER SECURITY. HIGHLIGHTS Overview of Cyber Stalking Understanding Security of Cyber Stalking Protecting Your Cyber Security The use of the Internet or other electronic methods to stalk or harass a person, group, or organisation is known as cyberstalking. False charges, defamation, slander, and libel are examples. Monitoring, identity theft, threats, vandalism, sex solicitation, doxing, or blackmail are all examples. Listen to this article Table of Content Overview 'UNDERSTAND' - a form for cyber security How can I report cyber crime in India? Overview What is cyberstalking explain? Cyberstalking is a crime in which someone harasses or stalks a victim using electronic or digital means, such as social media, email, instant messaging (IM), or messages posted to a discussion group or forum. What is cyberstalking with example? Post rude, offensive, or suggestive comments onl...